No products in the cart.
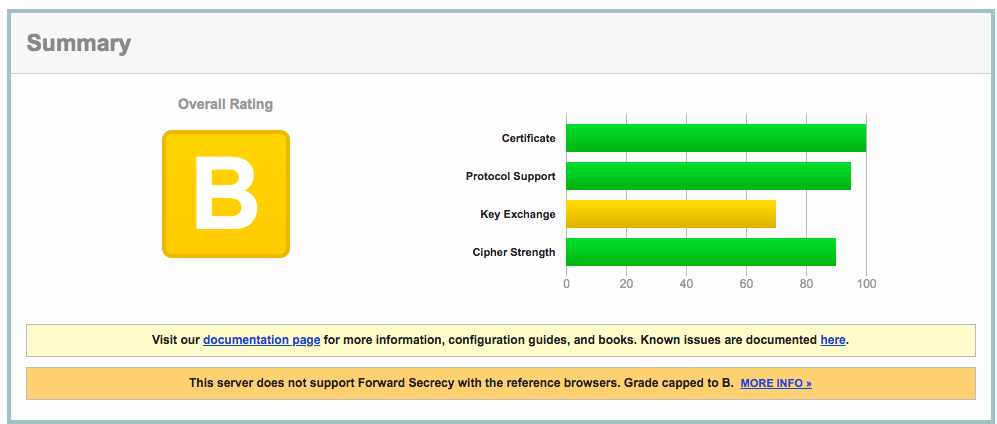
Good Enough Security Redux: SSL Inspection Devices Can Make Networks Less Secure A few months ago, I wrote about the concept of “Good Enough” security. This explored the thought that having DNS-based internet security is good enough to secure a network from most, if not all, internet-based threats. These technologies necessarily make....
Author
Latest Articles
 BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski
BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong
BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin
BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
Subscribe
Login
0 Comments