No products in the cart.
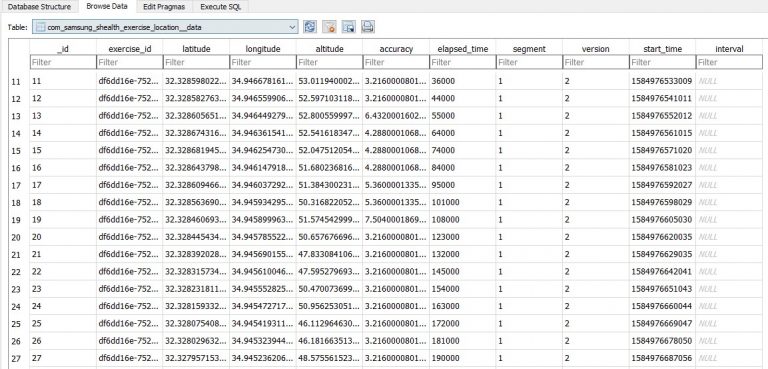
Decrypting Databases Using RAM Dump – Health Data Extracting memory from Samsung devices to decrypt Samsung Health DB’s can uncover critical data for investigators Samsung Health is a wellness application that helps users track their physical activities. As one might expect, the application stores a lot of interesting location data that....
Author
Latest Articles
 BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski
BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong
BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin
BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
Subscribe
Login
0 Comments