No products in the cart.
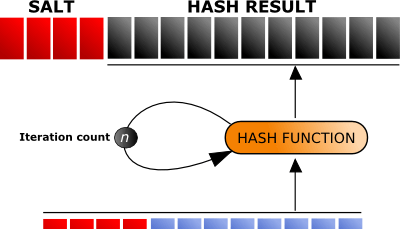
Many applications, operating systems, and other authentication mechanisms that take in credentials utilize a known defense against cyber-attackers known as "salting." For the non-IT or InfoSec professionals, whenever you create an account for any service, you more than likely created a password. Even though this is a known defense, it's....
Author
Latest Articles
 BlogApril 7, 2022Detecting Fake Images via Noise Analysis | Forensics Tutorial [FREE COURSE CONTENT]
BlogApril 7, 2022Detecting Fake Images via Noise Analysis | Forensics Tutorial [FREE COURSE CONTENT] BlogMarch 2, 2022Windows File System | Windows Forensics Tutorial [FREE COURSE CONTENT]
BlogMarch 2, 2022Windows File System | Windows Forensics Tutorial [FREE COURSE CONTENT] BlogAugust 17, 2021PowerShell in forensics - suitable cases [FREE COURSE CONTENT]
BlogAugust 17, 2021PowerShell in forensics - suitable cases [FREE COURSE CONTENT] OpenMay 20, 2021Photographic Evidence and Photographic Evidence Tampering
OpenMay 20, 2021Photographic Evidence and Photographic Evidence Tampering
Subscribe
Login
0 Comments