No products in the cart.
In this short excerpt from our Android Malware Analysis course by Tom Sermpinis you can learn how the Android Security Model works, what are the common infection vectors, and their detection methods. Interested in mobile forensics? This is for you!
The whole idea behind a mobile platform is the fact that the user can run a lot of different applications on the device. The user might be installing and downloading a banking application that can include some sensitive data. On the other hand, the user might be installing a game application right next to the previous application and running on the same device.
The user obviously does not want the game application to be able to access the sensitive data that the banking application is operating on. So to achieve this, the Android platform makes sure that any application is isolated from any other. Basically, when the user downloads and installs an application, it will be given a unique UID. In addition, each application will run on a separate process on a separate virtual machine. Therefore, applications cannot read any other application’s private data.
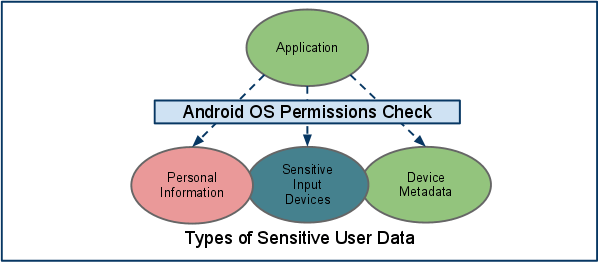
Image 4: Linux permissions for user data access.
Android was built on the top of Linux, so the Linux file permissions are applied. Permission allows the user to protect his/her sensitive data that are stored on the device. Also, it protects access to the content provider, which basically is a database in the device. Permissions are requested by an application at install time and they are granted or denied once at the install time, which requires user approval. In the next chapter, we will see the methods by which a device can be infected with malware.
Malware Infection Methods
There are several methods whereby Android devices could be infected with malware. The following are four different methods with which malware can be installed on the phone:
Repackaging legitimate application
This is one of the most common methods used by attackers. Repackaged applications, which are a category of fake applications, play a crucial role in the proliferation of mobile malware. Like fake apps, repackaged apps use social engineering tactics, displaying a similar user interface (UI), icons, package names and app labels as the legitimate/official version of the apps they spoofed. This is done to trick users into downloading fake apps and, consequently, generating profit.
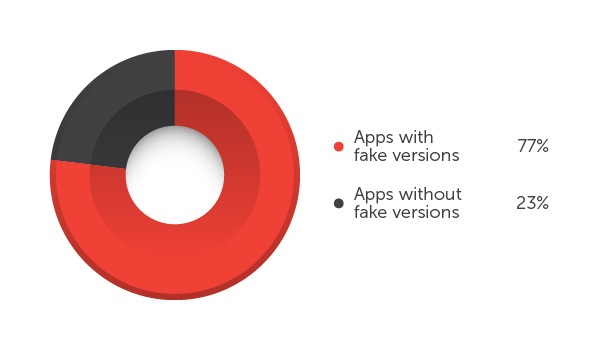
Image 5: Apps available in Google Play with and without fake versions
Based on the research, nearly 80% of the top 50 free apps found in Google Play have bogus versions. These apps can range from business, media and video, to games. In addition, more than half of fake apps today are tagged as ‘high-risk’ and ‘malicious’ due to the risk they pose to the users.
Several third-party app stores distribute repackaged apps, some of which are even Trojanized apps or apps that have been modified to add malicious code. Some samples include FAKEBANK, premium abusers, and Trojanized game apps. Cybercriminals add mobile ad software development kits (SDKs) in their bogus apps so as to generate income by pushing advertisements. Furthermore, they also change the mobile ad SDKs of legitimate apps just so they can get the earnings instead of the original developers. Another means of ‘trojanizing’ an app is by inserting malicious code into classes.dex file, which can introduce risks like malware infection and data theft.
Because of the security risks that repackaged apps pose to users, it is advisable for these app stores to include rules and audit mechanisms to control the propagation of fake/repacked apps. Google Play has implemented a rule preventing apps that are similar in terms of code and physical appearance with an already existing app.
Exploiting Android’s application bug
All applications are developed by humans, so it is really common to contain bugs. Many times these bugs/vulnerabilities can be exploited by an attacker to compromise an Android device and install the malware on the device.
Fake applications
It was also discovered that there are fake applications created to include malware that allow attackers to access your mobile device. Attackers upload on the market fake applications that seem legitimate to users but they are malware by themselves. For example, Spyeye’s fake security tool was found in the market which is a malware.
Tokyo-based Trend Micro, which makes antivirus and antimalware software that guard against such risks, said it cataloged 890,482 fake apps in a survey conducted in April of this year. More than half were judged to be malicious of which 59,185 were aggressive adware and 394,263 were malware.
Fake apps of this kind may be apps that have some usability or apps that don’t work at all, but infect your device. Most of the time, they can be found on fake app stores, or sometimes (mostly unlikely) in Google’s Play Store, if the attacker managed to fool Google’s safeguards.
Remote Install
The malware could be installed in the user phone remotely. If the attacker is able to compromise users’ credentials and pass them in the market, then in this case, the malware will be installed into the device without the user’s knowledge. This application will contain malicious codes that allow attackers to access personal data, such as contacts list.
Malware Detection Approaches
Now that we saw how a device can be infected, let’s see the approaches that we can follow to detect malware in infected applications. There are three different types of malware detection techniques:
- Attack or invasion detection
- Misuse detection (signature-based)
- Anomaly detection (behavior-based)
Attack or invasion detection tries to detect unauthorized access by outsiders. But misuse detection (signature-based) tries to detect misuse by insiders and describes very good detection results for specified, well-known attacks. The advantages of misuse detection are:
- It has no false positives
- It can quickly detect intrusion.
The disadvantage is that it is not capable of detecting new unfamiliar intrusions, even if they are built as minimum variants of already known attacks.
Continuing, anomaly detection (behavior-based) refers to detecting patterns in a given dataset that do not conform to an established normal behavior. It also attempts to estimate the abnormal behavior of the system to be protected and generate an anomaly alarm whenever the deviation between a given observation at an instance and normal behavior exceeds a predefined threshold. An advantage is the potential to detect previously unseen intrusion events and a disadvantage is many false positives and requires a large set of training data to construct normal behavior profile. For removing these shortcomings of misuse detection and anomaly detection, profiles should be updated with a large amount of the datasets at regular intervals of time. But a large amount of the datasets also increases the problem of inconsistency, redundancy and ambiguity. Several data mining techniques have been applied for intrusion detection. K-Mean Clustering is an unsupervised data mining technique for intrusion detection and it is easy to implement.
Three major drawbacks of K-mean clustering are:
- class dominance problem,
- force assignment problem, and
- no class problem. It has been observed that single model cannot give better result in terms of recall and precision.
In the next module, we will mainly deal with malware detection techniques, and start analyzing applications, using malware analysis tools, for malware infections.
[custom-related-posts title="Related Posts:" none_text="None found" order_by="title" order="ASC"]
Author
Latest Articles
 BlogApril 7, 2022Detecting Fake Images via Noise Analysis | Forensics Tutorial [FREE COURSE CONTENT]
BlogApril 7, 2022Detecting Fake Images via Noise Analysis | Forensics Tutorial [FREE COURSE CONTENT] BlogMarch 2, 2022Windows File System | Windows Forensics Tutorial [FREE COURSE CONTENT]
BlogMarch 2, 2022Windows File System | Windows Forensics Tutorial [FREE COURSE CONTENT] BlogAugust 17, 2021PowerShell in forensics - suitable cases [FREE COURSE CONTENT]
BlogAugust 17, 2021PowerShell in forensics - suitable cases [FREE COURSE CONTENT] OpenMay 20, 2021Photographic Evidence and Photographic Evidence Tampering
OpenMay 20, 2021Photographic Evidence and Photographic Evidence Tampering
Subscribe
Login
0 Comments