No products in the cart.

By: Adam Karim

FTK Imager, also known as Forensic Toolkit Imager, is a software tool commonly used in the field of digital forensics. It is developed and distributed by AccessData, a company that specializes in digital investigations and forensic software. FTK Imager is a free, standalone application that provides forensic professionals, law enforcement agencies, and computer forensic examiners with the ability to create forensic images of digital storage media, such as hard drives, USB drives, memory cards, and other storage devices.
Key features of FTK Imager include:
1.Disk Imaging: FTK Imager allows users to create forensic images of digital storage media. These images are bit-by-bit copies of the original media, preserving all data, file structures, and metadata for forensic analysis.
2.File Examination: It provides the capability to examine files within a forensic image without altering the original data. This includes viewing file attributes, directory structures, and file content.
3.Data Carving: FTK Imager can be used to recover deleted files or fragments from disk images through a process known as data carving. It can identify and extract files even if their file system metadata has been partially or completely erased.
4.Hashing: The tool can calculate cryptographic hash values (such as MD5, SHA-1, and SHA-256) for files and disk images, allowing forensic experts to verify data integrity and authenticity.
5.Memory Analysis: FTK Imager also supports the acquisition and analysis of RAM (Random Access Memory) from a live system, which can be crucial for volatile data analysis during forensic investigations.
6.Portable Version: FTK Imager is available in both installable and portable versions, making it convenient for forensic professionals to carry it on a portable device for on-site investigations.
FTK Imager is often used in conjunction with other forensic tools and is known for its reliability and effectiveness in digital investigations, such as in cases of data breaches, cybercrimes, and for corporate compliance.
Fundamental Questions for IT Forensics Experts Involved in Disk Imaging Tasks.
1. Questions about the forensic copy of the USB flash drive!
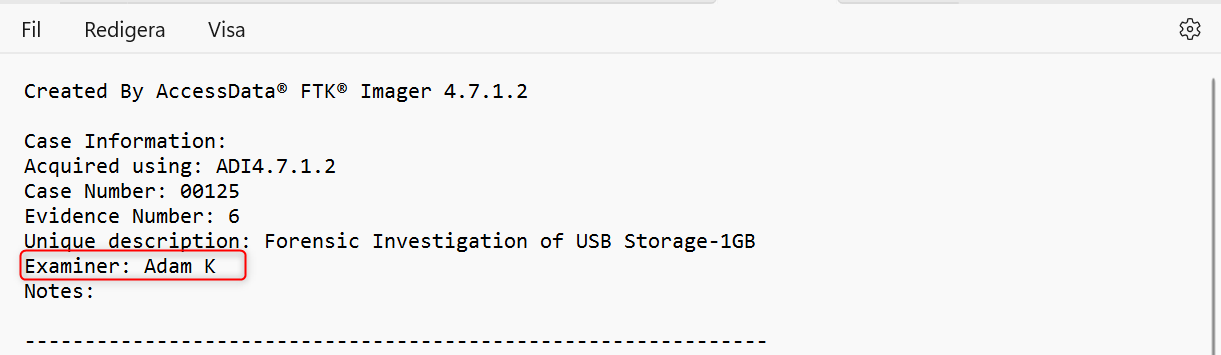
A) What is the name of the IT forensic scientist who has created a forensic image of the USB Flashdrive?
Answer: Adam K.
B) Was the information on the USB Flashdrive modified during the investigation?
Answer: The comparison does not indicate differences because both entities share identical hash values.
C) How to identify changes in file types on a USB flash drive using FTK Imager (See CCTV IP Cameras) ?
Answer:
The file named 'CCTV IP Cameras.pdf' does not have a matching file signature for a PDF. In the file content viewer, the signature 'JFIF' indicates that the actual format of the 'CCTV IP Cameras.pdf' file is an image, not PDF. Therefore, even though the extension is .pdf, the content is that of a JPEG image, suggesting that the file extension has been changed from .jpg to .pdf.
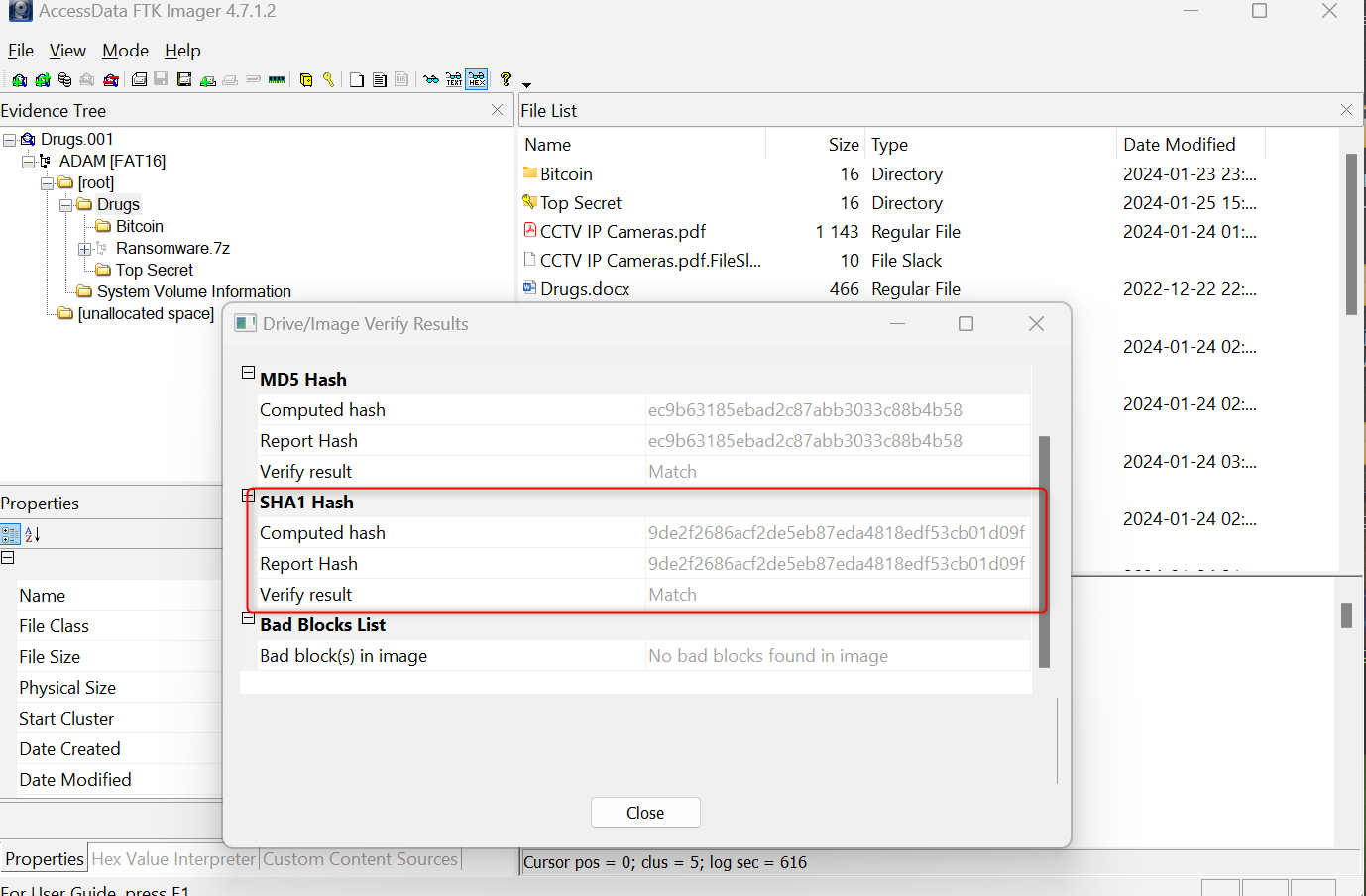
D) What is the SHA-1 checksum value of the forensic image created from the USB flash drive?
E) How much free space is there on the USB flash drive?
Right-click the disk image name and select (Image Mount) Mount Image then right-click the letter.
F) What file system does the USB flash drive use?
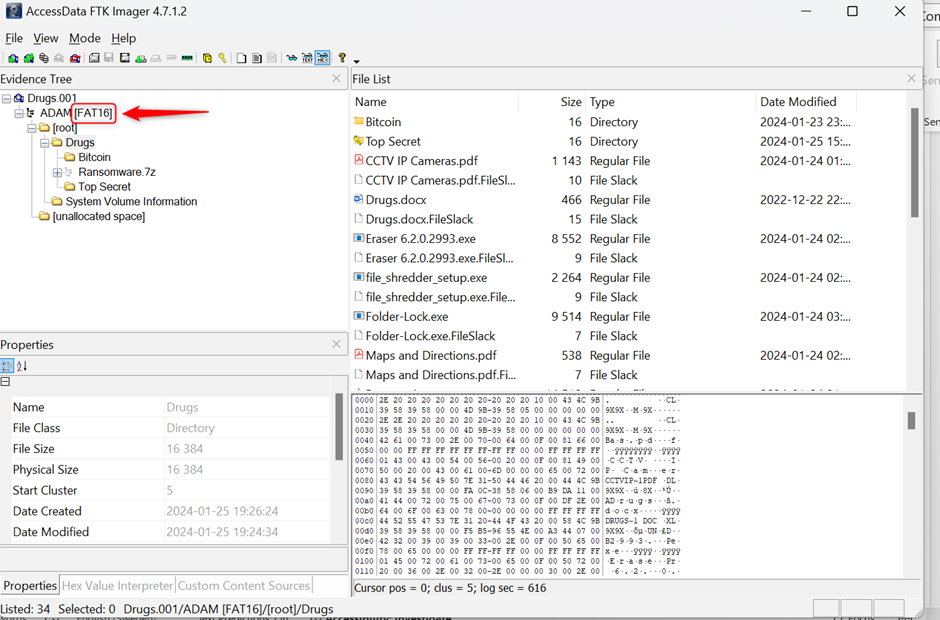
Answer:
FAT16
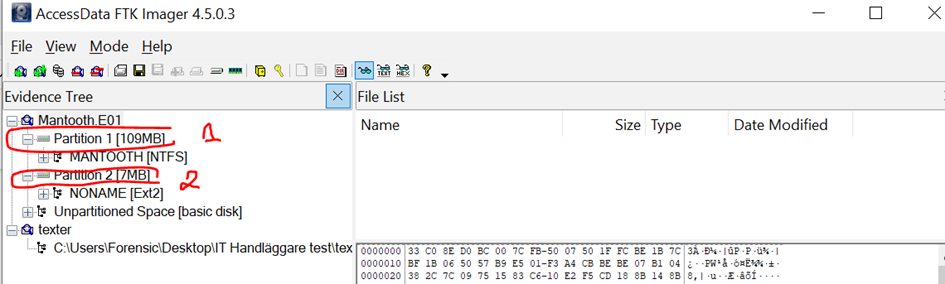
G) Are there any partitions on the USB flash drive, and what is the size of these partitions in the file system?
The USB Flashdrive does not display any partitions when inspected directly. However, I need to analyze the 'Mantooth.E01' disk image to understand the partition layout. According to the analysis, the disk image reveals two partitions: the first partition has a size of 109 MB, and the second partition has a size of 7 MB
H) Was the mirror copy of the USB flash drive created using a Linux, Windows, or Mac OS X system?
Answer:
To determine which operating system was used to create the mirror copy of the USB flash drive, we can examine the file system format of the copy. If the file system is FAT (such as FAT32 or exFAT), it is likely that the copy was created on a Windows system. If the file system is APFS, then the copy was likely created on a Mac OS X system. If the file system is EXT (such as EXT3 or EXT4), then it is likely that the copy was created on a Linux system.
I) What is the MD5 hash value of VeraCrypt.exe?
J) In the Bitcoin folder, there are five text files with Bitcoin addresses. Is it the same Bitcoin address on all files or are they different?
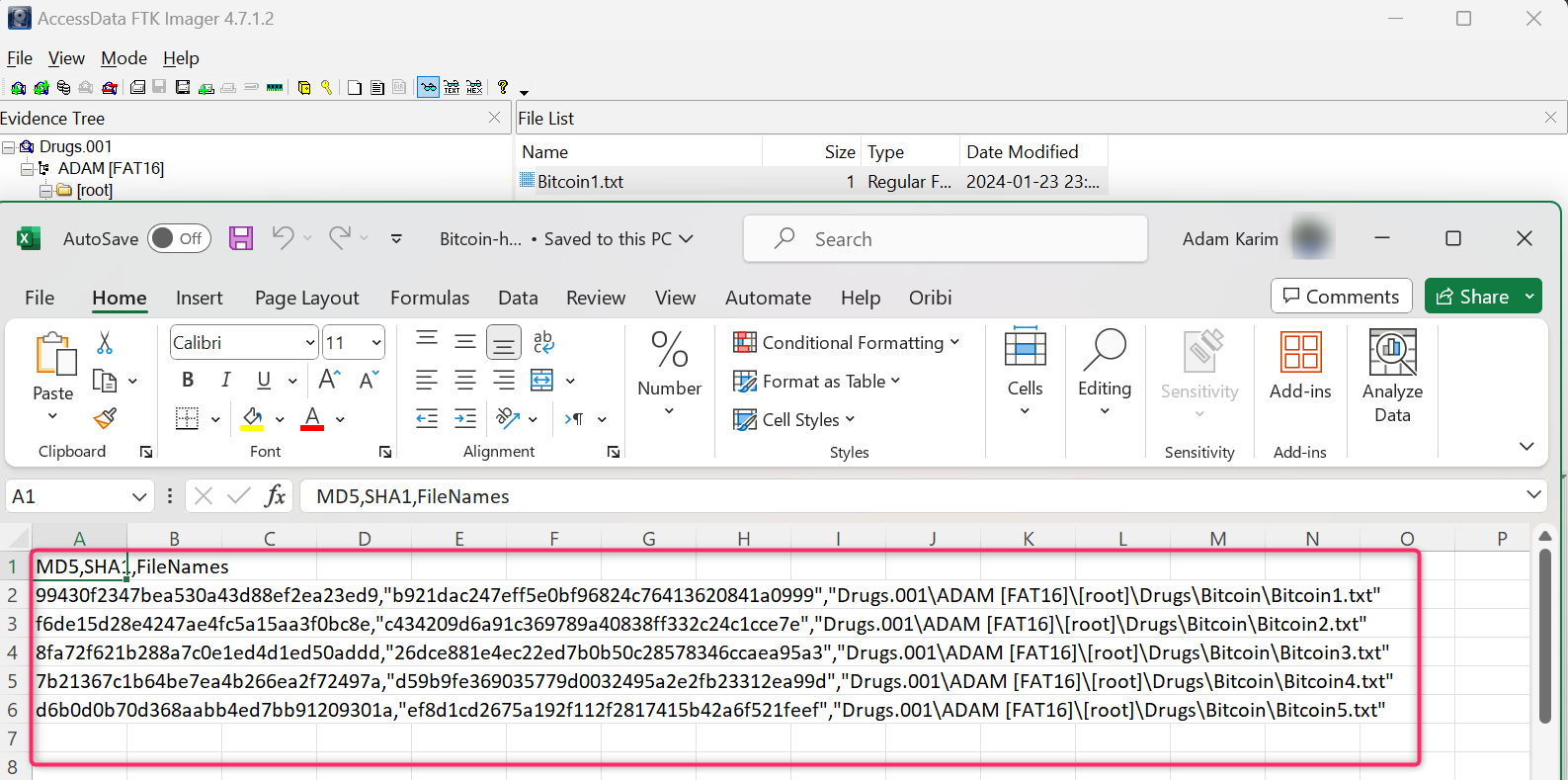
K) In what picture are the hidden passwords of the Ransomware.7z archive? (See Stockholm.jpg)
Answer:
P@ssw0rdA47
L) What is the decryption key of the Ransomware?
M) Under what name was the USB drive registered?
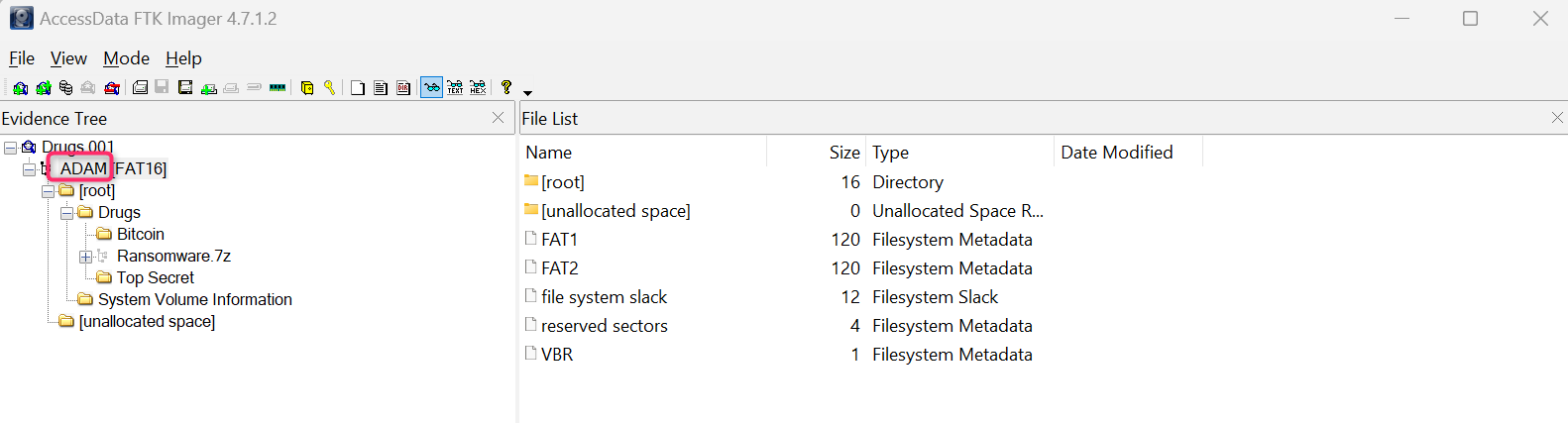
Answer:ADAM
2. Questions about metadata on a mirror copy of a USB flash drive?
A) Who and when was the Word document created?
B) Is the Word document signed by the same person who created it?
Answer: The Word document signed by Sasha
C) What is the path to the Word document?
3) Questions about deleted files!
A) In the context of using FTK Imager for digital forensic analysis, how can one determine if files have been marked as deleted within the tool?
Answer: In FTK Imager, deleted files are indicated by a red cross symbol next to their names.
B) Can FTK Imager be used to assist in the recovery of deleted photos?
Yes, it is often possible to recover deleted photos, especially if they haven't been overwritten by new data. When a file is deleted, the space it occupied is typically marked as available for use by new files, but until it is overwritten, the original data often remains and can potentially be recovered.
4.Questions about encrypted files!
A) Is it possible to identify files that have been encrypted with VeraCrypt or TrueCrypt using FTK Imager?
Yes, FTK Imager can be used to identify files or containers that may have been encrypted with VeraCrypt or TrueCrypt. While FTK Imager itself cannot decrypt these files, it can help you recognize potential encrypted volumes or files based on certain characteristics. Here's how you might identify them:
File Extensions: Encrypted volumes don't typically have a unique file extension, but users might use common extensions like .tc for TrueCrypt or custom extensions for VeraCrypt.
The .hc extension is commonly used and recognized by VeraCrypt.
B) Are there any encrypted files on the USB flash drive?
Answer: It appears that the file named 'Contact.txt' has been encrypted using the Encrypting File System (EFS) feature. EFS is a built-in encryption tool provided by Windows to help protect individual files and folders.
C) Can FTK Imager create an image of drives encrypted with BitLocker or with HPFS?
FTK Imager cannot create a forensic image of drives that are encrypted with BitLocker or formatted with the High-Performance File System (HPFS).
D) Does FTK Imager have the ability to create disk images from drives with NTFS, EXT, and HFS file systems?
Yes, FTK Imager possesses the capability to create disk images of drives formatted with various file systems, including NTFS (New Technology File System), EXT (Extended File System used in Linux), and HFS (Hierarchical File System used in macOS).
5.Questions about Unallocated Space!
A)Is it possible to manually recover deleted images from unallocated space without using any forensic tool? If so, how does it work?
Answer:
Yes, it is often possible to recover deleted photos, especially if they haven't been overwritten by new data.,
It is possible to manually recover deleted images from unallocated space in FTK Imager through a process known as file carving. File carving is a method used in digital forensics to recover files based on their content rather than their file system metadata, which can be useful when dealing with deleted files. Here's a more detailed explanation of how you can achieve this in FTK Imager using the JPEG file headers and footers:
1.Understanding JPEG Headers and Footers: JPEG files typically begin with the header FFD8FF and end with the footer FFD9. These hexadecimal sequences are used to identify the start and end of a JPEG file.
2.Using FTK Imager:
Open FTK Imager and load the image (disk image or physical/logical drive) containing the unallocated space you want to examine.
3.Navigate to the unallocated space. This is where files that have been deleted and are not currently allocated to any directory reside.
4.Searching for JPEG Headers:
Use FTK Imager's search functionality to look for the JPEG header FFD8FF. This will help locate the beginning of a JPEG file in the unallocated space. It’s important to note that there might be multiple occurrences of this sequence, as it could be present in various deleted JPEG files.
5.Carving Out the File:
Once you locate a header, you need to identify the corresponding footer FFD9 to determine the end of the image file. The data between these headers and footers is what constitutes the JPEG image.
6.Extracting the File:
After identifying the start and end of the file, you can manually select this range of data and extract it as a separate file. Save this data with a .jpg extension, and then you can attempt to open it with an image viewer to see if the recovery was successful.
For a detailed guide on how to manually recover deleted images from unallocated space using FTK Imager, please refer to my YouTube video. This video offers step-by-step instructions and visual aids that can help in better understanding the process.
6.Questions about FTK Imager
A) Can FTK Imager recover overwritten files?
Answer:
FTK Imager can effectively recover files that have been deleted but not yet overwritten, as well as files from damaged or corrupt partitions. However, if a file has been completely overwritten with new data, the original file cannot be recovered by FTK Imager or any other software tool. This is due to how data retention and overwriting work rather than a limitation of the specific software.
B) What types of evidence file formats can be created using FTK Imager?
Answer:
AD1(AccessData FTK Imager).
E01(EnCase Image File Format)
RAW (also known as "DD"),
AFF (Advanced Forensics Format)
C) After successfully exporting and creating a file hashlist using FTK Imager, what information is not included in this file?
Information such as date modification is usually not included in a default file hash list created with FTK Imager.
D) What file extension does the result get when creating a custom content image in FTK Imager?
Answer:
When creating a custom content image in FTK Imager, the result file usually gets the ". AD1'. The AD1 format is a specific file format used by AccessData, the company behind the FTK Imager, and it's designed to store both physical and logical images of data.
E) When FTK Imager is used to preview a physical drive, what number is assigned to the first logical volume in an extended partition?
Answer:
When the FTK Imager is used to preview a physical drive, the first logical volume within an extended partition is usually assigned the number 5.
References:
About the Author:

Adam Karim is a Computer Engineer specializing in Digital Forensics and IT Security. He is an ethical hacker and a professional penetration tester.
Subscribe
Login
0 Comments
