No products in the cart.
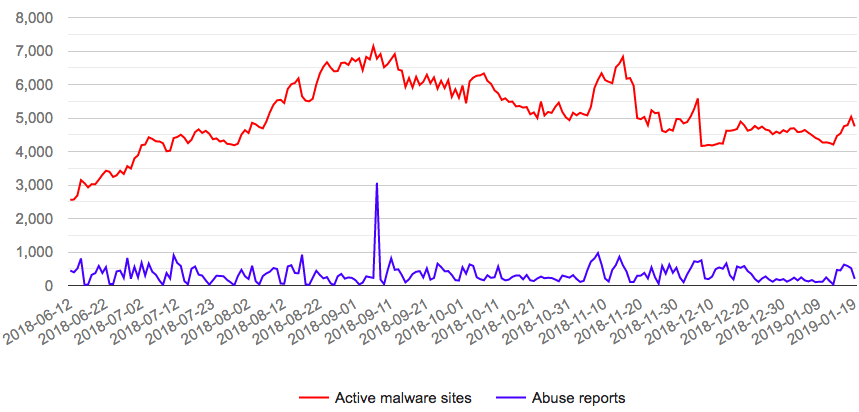
The Best Offense is Good Defense: Hosting Providers Remove Malware at Snail's Pace In March of 2018, a Swiss security researcher from abuse.ch began an initiative to take down websites hosting malware by contacting their hosting providers. The initiative was highly successful, taking down over 100,000 malware hosting websites in just 10 short months. A team....
Author
Latest Articles
 BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski
BlogSeptember 29, 2020Using the Google custom search engine for OSINT | By Maciej Makowski BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong
BlogSeptember 22, 2020Sysmon 12.0 — EventID 24 | By Olaf Hartong BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin
BlogSeptember 21, 2020Decrypting Databases Using RAM Dump – Health Data | By Michal Rozin BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
BlogSeptember 18, 2020TikTok — Using OSINT to Discover New Leads | By Josh Richards
Subscribe
Login
0 Comments