No products in the cart.
Cybersecurity
Cyberattacks and cybercrimes are multiplying around the world, and the methods used to do so are constantly evolving.
Digital Security and Privacy Tips
Look for a comprehensive checklist of over 300 tips to protect your digital security and privacy in 2024.
GPS Device Forensics as a Career Path?
GPS forensics involves extracting raw GPS data from devices like smartphones, tablets, vehicle navigation systems, fitness trackers, and other equipment with location-based service features. The data provides critical insights through time-stamped latitude, longitude, altitude, and speed records that can map out routes and stops.
ASU Studies Illegally Trafficked Bugs to Help Law Enforcement Catch Global Criminals
Surely, you’ve heard of the elephant tusk trade? Or rare jaguar skin that’s sold over the black market but have you ever heard of illegal bugs? These distinctive, contraband critters do exist, and they are trafficked illegally into the U.S. every year.

HOW TO INVESTIGATE FILES WITH FTK IMAGER
by Mark Stam The Master File Table or MFT can be considered one of the most important files in …
Finding Advanced Malware Using Volatility
FINDING ADVANCED MALWARE USING VOLATILITY by Monnappa Ka What you should know Basic understanding of malware Knowledge of operating system …
Windows Registry extraction with FTK Imager [FREE COURSE CONTENT]
There are several ways to perform an extraction from the Windows Registry, let’s see some of the most useful. This …
Installing Autopsy 4.6.0 on linux | by Christian Kisutsa
Installing Autopsy 4.6.0 on linux by Christian Kisutsa Autopsy is a digital forensics tool that needs no introduction. It has …
Forensic Investigation of Storage Media
Tools and Procedures for Forensic Investigation of Storage Media Deivison Franco, Cleber Soares, Daniel Müller, and Joas Santos Digital data and …
Introduction to Mobile Forensics
Lesson one Tutorial 1. Introduction to Mobile Forensics of the online course "Advanced Smartphone Forensics" Check here >> Mobile Forensics …
File System Analysis with Binwalk | By Alex Ocheme Ogbole
File System Analysis with Binwalk Binwalk is a simple Linux tool used for analysis of binary image files. Analyzing binary image …
ELA Photo Forensics
By: Pierluigi Paganini from Infosec Institute Error Level Analysis is a forensic method to identify portions of an image with …
Setting up a report template for OSINT investigations [COURSE MODULE 0]
In this short little video our instructor Josh presents his template for OSINT investigations. You can see what sections are …
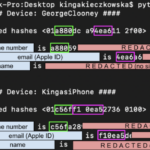
AirDrop Forensics | by Kinga Kięczkowska
AirDrop Forensics ✨ Welcome to AirDrop forensics! ✨ Let’s start with the basics: what is AirDrop? It’s a file-sharing service …
Profil3r | Rog3rSm1th
Profil3r by Rog3rSm1th Discord 💬 pip3 install profil3r && profil3r --help Find the profiles of a person on social networks, …
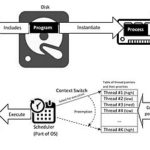
Windows Process Internals: A few Concepts to know before jumping on Memory Forensics [Part 3] – Journey in to the PsLoadedModuleList ( Loaded Kernel Modules) | By Kirtar Oza
Windows Process Internals: A few Concepts to know before jumping on Memory Forensics Part 3 – Journey in to the …
CyberChef Walkthrough [FREE COURSE CONTENT]
In this short tutorial by Cordny Nederkoorn, the instructor of our MacOS Anti-Forensics course, you will learn how to use CyberChef …
How EnCase Software has Been Used in Major Crime Cases (Plus how to use EnCase Forensic Imager Yourself) | By Brent Whitfield
How EnCase Software has Been Used in Major Crime Cases (Plus how to use EnCase Forensic Imager Yourself) As with …
Practical Guide to USB Forensics - Data Breach Test Case by Tal Eliyahu
Computer forensics is the process of obtaining digital information and analyzing it for any leaked or stolen data. Basically, it …
Setting up Security Onion at home | By Z3R0th
Setting up Security Onion at home First off, what exactly is Security Onion and why do I care about this? …
Breaking LUKS Encryption | By Oleg Afonin
Breaking LUKS Encryption LUKS encryption is widely used in various Linux distributions to protect disks and create encrypted containers. Being …
Windows Process Internals : A few Concepts to know before jumping on Memory Forensics | By Kirtar Oza
Windows Process Internals : A few Concepts to know before jumping on Memory Forensics I have been revising memory forensics …
What is a Sock Puppet Account And Why Do We Need One?
When it comes to OSINT investigations, surveillance, and other searches, the use of a sock puppet account(s) is a critical …
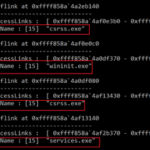
An Introduction To Memory Forensics: Windows Process Internals | by Joseph Moronwi
An Introduction To Memory Forensics: Windows Process Internals by Joseph Moronwi Our ability as forensic investigators to efficiently and effectively …
Interview with Kunal Dutt
In myriad cases, digital forensics comes into the picture, but the most generic answer would be “when the cyber security infrastructure fails somewhere around the cause of vulnerabilities, to identify and trace down the entire incident of this failure would be a process done by this glorious department known as digital forensics“
Incident Response and Forensics Foundamentals in AWS - LIVE WEBINAR with Afshan Naqvi
Welcome to the first live webinar by eForensics Magazine. My name is Bartek and I'm responsible for organizing online courses, mostly for PenTest Magazine and for Hackin9 Magazine, but also the most recent course of eForensics, which is instructed by Ms. Afshan Naqvi, who is present with us today.
Interview with Dauda Sule
You must be able to conduct lab exercises for students, particularly in digital forensics, and hold a minimum of a bachelor's degree in cyber security or a related discipline. You would definitely need to be able to demonstrate digital forensics skills with tools such as FTK Imager, Autopsy, and Wireshark, to name a few.
DFIR Labs in the Cloud: The Future of Digital Forensics
In this article, we will cover the ins and outs of adopting cloud solutions in digital forensics and explore how DFIR tools can accommodate this change. As an example, we will look into Belkasoft digital forensics software, known for its innovative solutions, and explore the features that enable it to embrace the cloud approach.

DFIR in AWS (W63)
This course provides a crucial skill set in securing AWS environments. In today's digital landscape, understanding digital forensics, incident response, and automation in AWS is essential for safeguarding data and infrastructure. This course offers hands-on experience, making it an invaluable asset for those eager to enhance their cybersecurity expertise and stay ahead in the dynamic field of cloud security.
Deepfake Audio: A Comprehensive Study in Digital Forensics Course Online (W62)
This course is aimed at presenting an elementary yet comprehensive picture of the field of digital audio forensics, with the implied hope that it will afford the participant useful theoretical and practical knowledge of the field and its various aspects.
Micro-drone Warfare: Cybersecurity Implications and Countermeasures (W61)
"Micro-drone Warfare: Cybersecurity Implications and Countermeasures" is an advanced course designed for digital forensics professionals seeking to understand the cybersecurity challenges posed by the increasing use of micro-drones in modern warfare. The course provides an in-depth exploration of micro-drone technologies, their role in cyber threats, and the countermeasures necessary to mitigate these threats. Learners will delve into the various types and capabilities of micro-drones, their communication and networking technologies, and the associated cybersecurity vulnerabilities. The course covers risk assessment and threat modeling for micro-drone systems, analysis of real-world micro-drone warfare scenarios, and the development of defense strategies against potential cyber attacks. Additionally, the course addresses the legal and policy frameworks governing micro-drone warfare cybersecurity, including ethical considerations, privacy implications, and international regulations. The course is led by Rhonda Johnson, a seasoned educator and Ph.D. student specializing in Cybersecurity. Prior knowledge of computer networks, cybersecurity principles, operating systems, basic electronics, and wireless communication is recommended. The course employs tools such as Drone Simulators and Drone Performance Evaluation Tools for practical learning.
Data Integrity And Evidence Handling in Digital Forensics - Course Online (W60)
The course is intended for individuals from the IT industry as well as those outside of it who have some knowledge of cybersecurity. Basic concepts of cybersecurity are required. During the course, participants will acquire skills related to: Understanding digital forensics, including its scope, relevance in investigations, and legal and ethical considerations. Concepts of data integrity and its significance in digital forensics. They will learn about various threats to data integrity and techniques for ensuring its preservation throughout the forensic process. Principles of evidence handling, including chain of custody, documentation, and the importance of maintaining the integrity of evidence. Legal and ethical considerations related to digital evidence handling. This includes understanding privacy and confidentiality considerations and the role of expert witness testimony in courtroom presentations. Data acquisition techniques for different types of digital devices. They will learn about disk imaging, integrity verification, and the use of hash functions in maintaining data integrity. Techniques for analyzing and examining digital evidence, including file system analysis, data recovery, reconstruction techniques, and metadata analysis. The course also includes practical application of various tools and technologies used in digital forensics, such as Autopsy, The Sleuth Kit (TSK), Volatility, Plaso, Wireshark, Bulk Extractor, OSForensics, and Autopsy Browser. At the end of the course, a final exam is planned consisting of multiple-choice questions on the concepts and fundamentals arising from the course outcomes, along with practical tasks.